Classical Ciphers to Digital Signatures Wolfram U Launches New Cryptography Course

Cryptography has been around since time immemorial, and in the modern technological age is an omnipresent, often invisible middleman that helps protect your data. As a field of study, it combines mathematics, computer science, physics and even linguistics. As a tool, it concerns informatics, business, finance, politics, human rights—any sector that deals with personal information or requires communication. In fact, it’s hard to imagine a sector that cryptography does not impact.
Today, I am happy to announce a new, free interactive course, Introduction to Cryptography, that will help students around the world get a grasp on the variety of topics this vast field offers. The Wolfram Language allows the course to deliver unique hands-on material and address questions such as “How can I secretly transmit information between two people?” and “How do cryptocurrencies operate without a central authority?”
I also invite you to start exploring the interactive course by clicking the following image.
Motivation from History
Ever since writing was invented, people have been interested not only in using it to communicate but to conceal the content of messages from those they do not trust. For centuries, the alchemy of private communication was an art known to few. It was certainly not as important in the everyday life of most people then as it is now, but has always been an ever-present tool for gaining military or political advantage throughout the history of humanity.
Since World War II—and especially with the rise of the internet—cryptography has grown beyond encryption alone to include a group of special-purpose algorithms. These sustain the wider infrastructure of information security, such as user and message authentication and protection from illegitimate changes to messages and eavesdropping. In the past 50 years, cryptography has become a science, the workings of which this course covers.
Overview
Students taking this course will receive an introduction to the fundamentals of cryptography within the larger context of information security. Much of the course focuses on indispensable cryptographic algorithms in wide use: hash functions, secret-key encryption, public-key cryptosystems and digital signatures. Introduction to Cryptography also discusses some more advanced applications of cryptography, such as blockchains and secure password storage.
Here’s a sneak peek at some of the course topics (shown in the left-hand column):
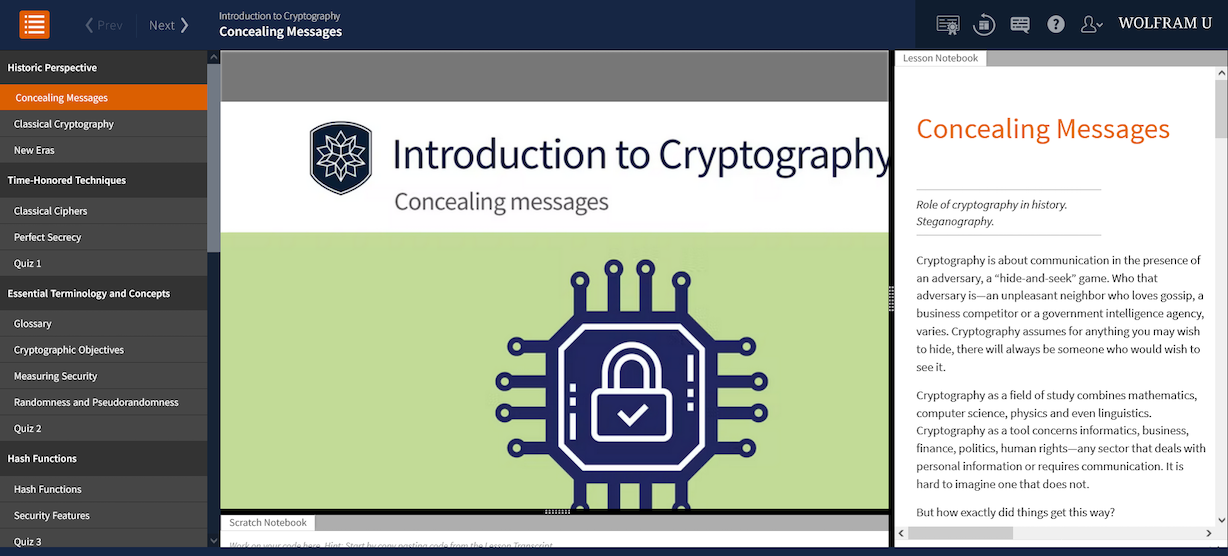
The course consists of 25 video lessons, averaging about 10 minutes each, supplemented with roughly 150 pages of written material in interactive notebooks. Working at a steady pace, students should be able to finish watching all videos and complete the six quizzes in six to eight hours.
I intentionally tried to keep the lessons self-contained; however, a basic understanding of computer science, algebra and modular arithmetic will be helpful.
The rest of this blog post will describe the different sections of the course in detail.
Lessons
The course has 25 lessons, beginning with the “Historic Perspective” section. It consists of three lessons that present the history of and milestones in the field, all the way from Caesar in ancient times to the twentieth century, where cryptography has played a crucial role in war outcomes and affected human lives more than ever.

The core of the course is dedicated to the fundamental tools of cryptography: hashes, secret-key ciphers, public-key encryption and signature schemes. Each concept and cryptosystem is introduced within the context of the information security objectives it is meant to achieve, where it is used in real-world scenarios and applications, and its pros and cons in comparison to other algorithms.
Each of the 25 videos is supplemented by a detailed transcript notebook displayed on the right-hand side of the screen. You can copy and paste Wolfram Language input directly from the transcript notebook to the embedded scratch notebook to try the examples for yourself.
Quizzes
Most sections of the course end with a short, multiple-choice quiz with 10 questions. A student who reviews the section carefully should have no difficulty in doing well on the quiz.
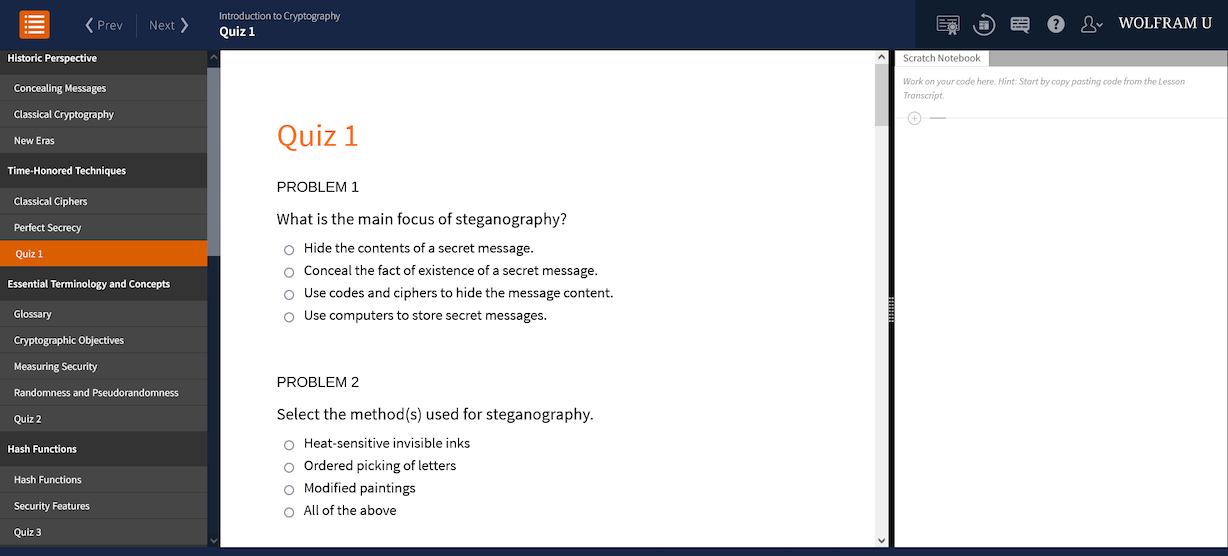
Students will receive instant feedback about their responses to quiz questions, and they are encouraged to go back to a section’s lesson notebooks for reference and to review the material as many times as needed.
Course Certificate
I strongly encourage students to watch all the lessons and attempt the quizzes in the recommended sequence because each course topic builds on earlier concepts and techniques. Plus, each new cryptosystem is presented with respect to the issues it solves compared to ones already discussed. You can earn a certificate of completion, pictured here, at the end of the course.

A course certificate is earned after watching all the lesson videos and passing all the quizzes. It demonstrates your understanding of the fundamentals of cryptography and will add value to your resume or social media profile.
A Building Block for Success
In the modern world of digital communications and interconnected remote systems, an understanding of the fundamental concepts of cryptography is undeniably useful for students of computer science and engineering, as well as for professionals. I hope that Introduction to Cryptography will help you to achieve mastery of information security and allow you to store and transmit data in your business or applications more securely.
For students who wish to dive deeper into mathematical and technical details, almost every lesson notebook points to relevant literature on its topic. At the end of the course, I have also provided a list of textbooks that greatly aided my own path in studying cryptography and preparing this course.
I have enjoyed teaching the course and welcome any comments about it as well as suggestions for future courses.
Acknowledgements
I would like to thank Konstantin Kouptsov for being the technical editor-in-chief and Cassidy Hinkle, Abrita Chakravarty, Veronica Mullen, Tim Shedelbower, Joyce Tracewell and Amruta Behera for their dedicated work on various aspects (visuals, quizzes and videos) of the course.
I would also like to thank the professors at my alma mater, the Igor Sikorsky Kyiv Polytechnic Institute, for instilling a love for cryptography in me years ago. Those initial steps began the journey that ultimately led to the creation of this course.
| Want more help? Register for one of Wolfram U’s Daily Study Groups. |




Comments